Cyber security researchers are apprehensive that a Russian cyber espionage operation behind the hacking incident into Democratic National Committee in the run-up to the 2016 US Presidential election that remained docile till now has woken up with a series of attacks against government departments across Europe with the next US presidential race a year away.
The group known as Cozy Bear or APT29 is long believed to be an associated offspring of the Russian intelligence service and, alongside Russian military hacking group Fancy Bear, was involved in many high profile attacks between 2014 and 2017 team of cyber security analysts at ESET have come out with details of the group's renewed activities under a new campaign nick-named Operation Ghost. Referred as Dukes, they are active in attacks using the four new families of malware. MiniDuke targeted at three ministries of foreign affairs in Europe and an embassy of a European Union country in Washington DC. It is learnt that the group is active during the Russian daytime.

They first attack with targeted spear-phishing emails designed to lure victims into clicking a malicious link or downloading malware via an attachment use three other new families of malware named PolyglotDuke, RegDuke and FatDuke.
PolyglotDuke uses Twitter, Reddit, Imgur and other websites to link to their command and control (C&C) infrastructure, to avoid storing information in the malware and evade being detected. RegDuke contains the main payload and stores it on the Windows registry while also applying stenography to stay hidden. The third FatDuke, is a sophisticated backdoor with the ability to steal login credentials and other private data. ESET researchers have discovered an operation dubbed "Ghost," which started much earlier, in 2013, and is still ongoing. Here's a table compiled by ESET about their attacks over a period of time:
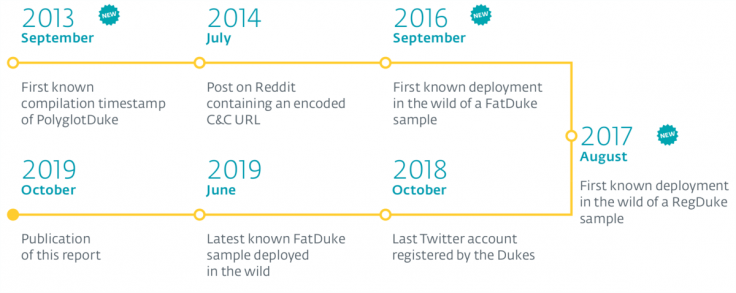
Matthieu Faou, ESET malware researcher said:"One of the first public traces of this campaign can be found on Reddit in July 2014," says ESET researcher Matthieu Faou. "We can confirm with high confidence that the same group is behind Operation Ghost and the DNC attack."
The ESET team is planning to monitor activity by Dukes and post a list of Indicators of Compromise on GitHub. The team also doesn't rule out the possibility of Cozy Bear to return again in future. "We can expect them to develop new tools to be able to re-start their attacks in the next weeks or months," said Faou. However, it is believed among the cyber security experts that the Russian hackers cannot be stopped for the next 20 years.









