The ongoing Coronavirus pandemic has opened up new avenues for cybercriminals to exploit users, steal data and even launch ransomware attacks. Among them, particularly vulnerable is your smartphone.
With Coronavirus apps dominating Google's Play Store and Apple's App Store, many users have downloaded apps from unofficial sources which could put their data at risk. On Friday, June 12, Singapore Computer Emergency Response Team aka SingCert warned the citizens of fake apps which could imitate the city-state's contact tracing app TraceTogether.
A wing of Singapore Cyber Security Agency, SingCert said that hackers are exploiting the interest in the app and are conducting "malicious activities through fake mobile applications that imitate official COVID-19 contact tracing applications."
Anomali study
SingCert's warning came after the American cybersecurity company Anomali released a study which identified 12 fake apps targeting 11 countries. Two of the fake apps mimicked Singapore' TraceTogether with two trojan payloads getting installed on devices. Such apps' logos look identical to the official app but are malicious.
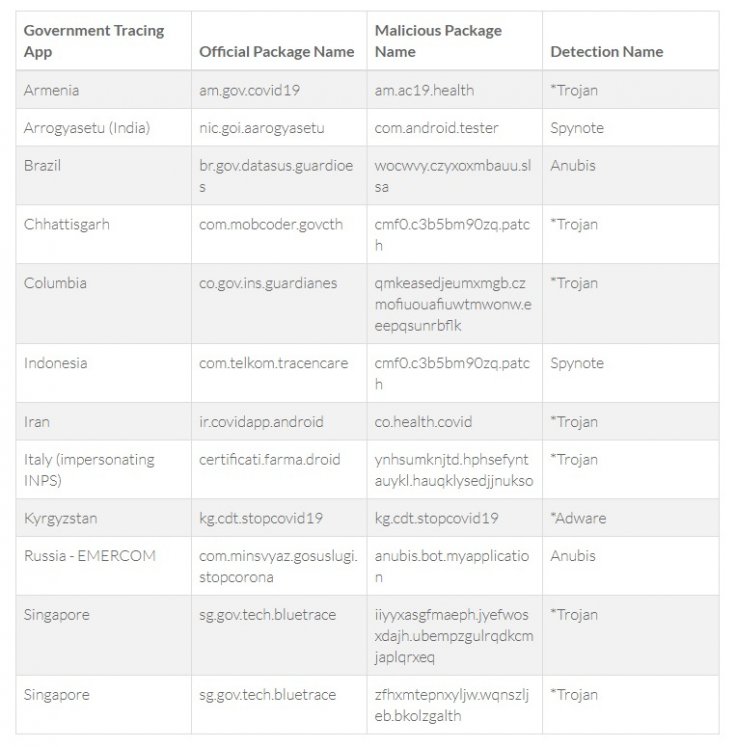
Apart from that, India's Aragyasetu app, official contact tracing apps of Armenia, Brazil, Columbia (a state on the U.S.), Indonesia, Iran, Italy, Kyrgyzstan, Russia and one from the Indian state of Chhattisgarh are among the targets, it said.
In recent times, cyberattacks related to Coronavirus have seen a huge surge. According to Google, approximately 18 million phishing emails have been received on its email client Gmail while 240 million spam messages have been circulated daily since April this year.
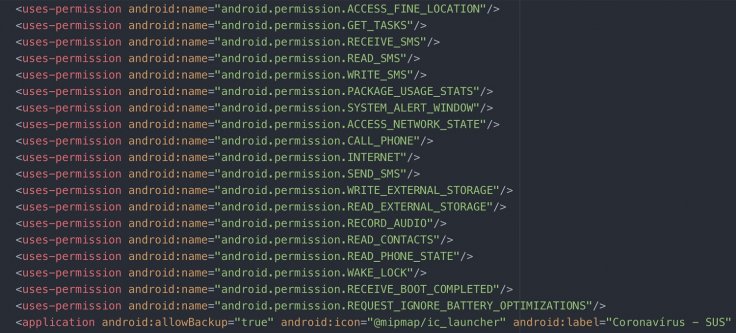
"These fake applications are usually embedded with trojans or malware that, when executed, could be used to monitor user's activities on the device and/or steal their personal data," said SingCert in a statement.
What are Anubis and SpyNote?
Hackers are using two malware components -- Anubis and SpyNote -- in their app scripts to launch the attacks. SpyNote, an Android trojan, collects and monitors data on the devices while Anubis is a financial trojan that can access and steal users' banking credentials. It can disguise itself as legitimate application and fake software updates.
"The global impact of the COVID-19 pandemic makes the virus a recognizable and potentially fear-inducing name, of which actors will continue to abuse," Anomali said in the study.
Don't Trust Unofficial Channels
While Google's Play Store and Apple's App Store do not host such apps, the threat comes from the unofficial platforms and third-party app stores. SingCert warned the users to refrain from downloading apps from such places and to check the credentials of the developers. It also urged users to check the permissions apps may ask. If found suspicious, users should not download such apps, warned the 'threat intelligence' firm.
"Check the developer information on the application listing. Only download applications developed and listed by the official developer. Look through the application's reviews, and be wary of poorly-reviewed applications. Multiple poor reviews or comments may be an indication of issues with the application," SingCert added.
For those who have already downloaded such apps from unofficial sources, they should immediately delete them and run an antivirus scan, SingCert advised. If unable to delete the app after installation, the user should perform a backup and factory reset on the device as per the agency.









