Despite new breakthroughs in cybersecurity and improved malware detection tools, hackers always find a way to exploit the loopholes. Now, they have found a new way to launch their attacks against companies – through resume or curriculum vitae (CV) and sick leave applications.
The Coronavirus pandemic has seen a massive rise in both new job seekers and medical leaves. And hackers have started exploiting both. According to new research by Checkpoint, hackers are hiding malware in CVs disguised in a job application and medical leave emails to companies.
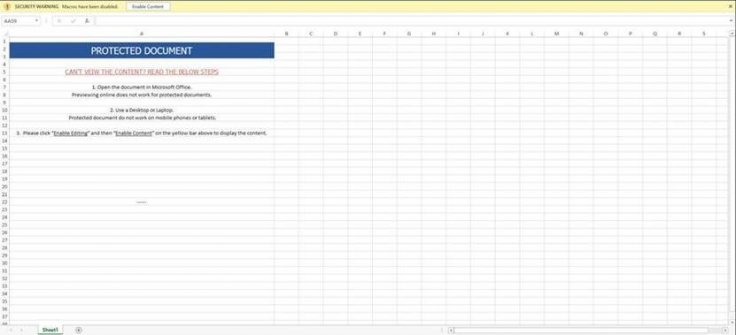
According to cybersecurity company Check Point's study, banking Trojans 'Zeus', 'Zloader', 'Icedid' and 'Trickbot' are hidden in malicious Excel (.xls) or Document (.doc) files in emails. Such emails usually come to the inbox with subject lines of "applying for a job" or "regarding job,". When clicked on the attachment files, a malicious macro starts running and download the malware payload. Once it is installed, it steals banking information and financial transactions. Hackers also use different sender domains to deceive the filters in email clients.
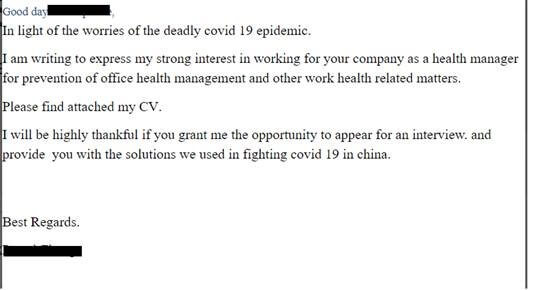
In the U.S., hackers have also found a way through the U.S. Family and Medical Leave Act (FMLA) to reach the inbox and trick the administrative staff. "Now that the world is seeing some relief from the pandemic as a result of the quarantine measures, things have started to open up and businesses are running again and – guess what? – cyber-criminals are also ramping up their malicious activities. In May, we saw a 16% increase in cyber-attacks when compared to the period between March and April, when coronavirus was at its peak," Check Point said.
Rise in Coronavirus Related Attacks
After such malware emerged in 2016, the uses of such payload gradually diminished. But COVID-19 pandemic has brought them back to life again with millions of such emails hitting the inboxes of small to big companies targeting the relief packages they received from their respective governments.
According to Google, its popular email client Gmail received over 18 million phishing emails daily since April. That is in addition to over 240 million spam messages relating to Coronavirus scams. Check Point study found that after the U.S. Government announced a stimulus package for small businesses in April, such companies and its owners saw a surge in the number of spam emails. It indicates that hackers were targeting people who had received the payments.
"In March 2020, a total of 2081 new domains were registered (38 malicious; 583 suspicious). In the first week of April – 473 were registered (18 malicious, 73 suspicious). After the American government proposed the stimulus package to taxpayers, the number of new domains registered that week was 3.5 times higher compared to the average of previous weeks," the study found.
However, overall, there has been a 30 percent decrease in the total number of cyberattacks compared to last year. This is due to the fact that in many countries offices were closed as a result of full or partial lockdown.

How to Stay Protected
While despite using the best web protection and anti-malware software and email filters, you can be tricked, here are some tips to avoid such instances.
- Don't open emails from lookalike domains or emails with spelling errors
- Don't open files received via email from unknown senders
- Order goods only from trusted sources
- Don't click on promotional links in emails
- Don't click on 'Special Offers' as they are the best way to lure people
- Don't click on links that resemble 'Exclusive cure for coronavirus'
- Use different passwords for applications and accounts









