U.S. President Donald Trump's COVID-19 diagnosis has attracted a lot of attention worldwide. As information from the White House was hard to come by, people, irrespective of their political ideologies, scrambled through the internet for any updates they could get. And that was a golden opportunity for hackers, who targeted people with spearphishing attacks.
As the media devoted a lot of coverage to Trump's hospitalization, his supposed treatment plans and eventual return to the White House, hackers designed phishing emails to provide updates on his health, tricking users into clicking on malicious links. The emails claiming to have more information about the President's health, come with a document attachment and force the user to download the file using a malicious link.

Potential Ransomware Attack
The emails come with subject lines such as "Newest information about president's condition" and when clicked on the link, takes the user to a legitimate Google Docs domain (docs.google.com) to download a file. Hackers give the impression that the file has been scanned and mark the document as "Safe" in green letters. However, it doesn't download a Word file. Rather, it downloads a BazarLoader executable file.
BazarLoader (also known as BazaLoader) is a trojan that creates a backdoor for hackers for future access. That way, attackers can download malware payload later that will encrypt the system for ransom or steal files and spread to the network the computer sits on.
As per ProofPoint, a cybersecurity firm, it eventually leads to the Ryuk ransomware attack. The same malware was used in the cyberattack on UHS (Universal Health Service) hospitals last month. In the past, Ryuk has been associated with a Russian hacker group named Wizard Spider that targeted large enterprises.
ProofPoint researchers believe BazarLoader has been created by the same group that was behind TrickBot. The malware has been used extensively during the Coronavirus pandemic to lure users with phishing emails such as job opportunities or COVID-19 relief package from the governments.
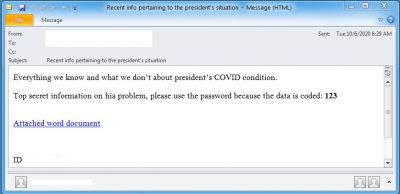

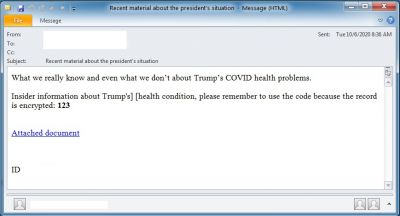
As revealed by another cybersecurity research firm Check Point, hackers targeted big to small enterprise administrative staff with phishing emails disguised as job applications and applications for medical leave. When the attached Document or Excel file is downloaded, it runs a macro leading to the download of the malware payload. The method was used to steal sensitive data and also ransomware attacks as it could infect other computers on the network.
Emotet Malware
However, Trump's health isn't the only mode to deliver the malware payload. Last week, ProofPoint also noticed an increase in malware attacks through emails pretending to be from the Democratic National Convention's Team Blue campaign. Hackers targeted American voters with such phishing emails, tricking users to download files that will lead to downloading the Emotet malware.
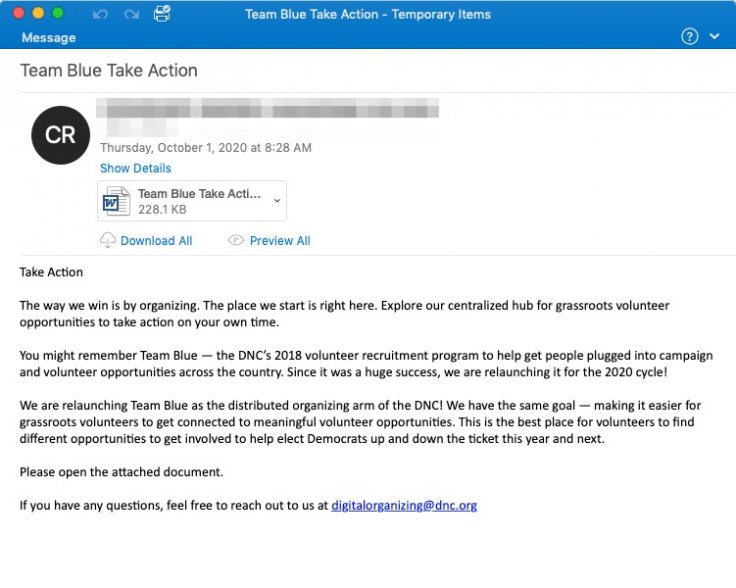
ProofPoint noticed an increase in such attacks following the U.S. Presidential Elections debate. Here, although the theme of the attack is related to either U.S. Presidential Election or Trump's health, any popular topic such as Black Lives Matter protests or climate change could be weaponized for phishing attacks.









