Following the U.S. Presidential Election results, Donald Trump's campaign launched multiple lawsuits in different states, alleging voter fraud. To prove that, the campaign team and Trump's lawyers turned to the voters by creating new websites so that people can easily report any irregularities. However, one such website has been found to leak voter data.
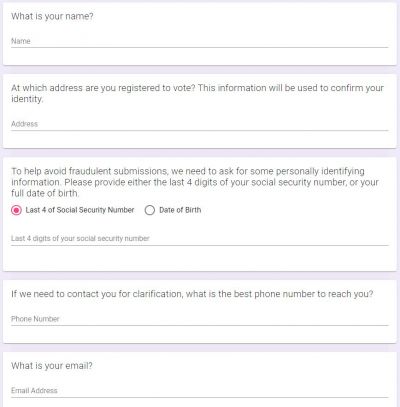
The website named "donttouchthegreenbutton.com" was launched in Arizona's Maricopa county for people to report "rejected votes." It collects personal information of voters including name, address, phone number, date of birth, email address and the last four digits of the social security number (SSN). The Google form on the website lets people search for their names and other details are automatically populated.

However, some users noticed that the website had an SQL injection vulnerability. Using the technique, someone could pull out personal information such as names, addresses, DOB and last four digits of the SSN. "On a lark, I went to the site and was looking at it and started adding a made-up name and noticed I was being shown names and addresses of voters. I played around a little more and realized just how bad this looked," a Reddit user, who noticed the vulnerability said.
Bulk Data Collection
While voter data is publicly available information and anyone can access it, the issue raises obvious privacy concerns. By using a simple technique, a hacker can get a bulk of information that can be used for phishing scams. BleepingComputer found that the data for the website was generated from the server through Algolia REST API. However, both the API key and Application ID were left exposed, making it easy for anyone to scrape the voter data in bulk.

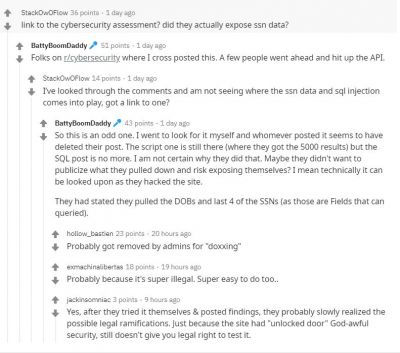
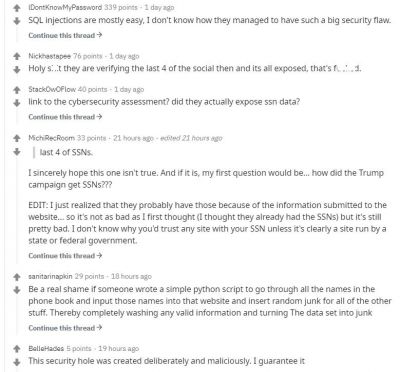
As the JSON data contains a list of five voters' information by default, bad actors could alter the query and download information repeatedly using a different combination of letters. "Someone ran a script to test out how easy it would be to pull the data and change the parameters to start with the letter 'A' and to stop at the first 5,000 entries and bam, the first 5,000 names and addresses," the user added.
However, after many reported the vulnerability to the Arizona Board of Elections and Maricopa county recorder, the Trump campaign fixed the issue and removed the API. But since it took over 12 hours to fix the issue, bad actors could scrape data from the site. This is, however, not the first time an election campaign leaked voter information. Democratic nominee Joe Biden campaign's Vote Joe app also had similar flaws.









