A team of IT security researchers from ThreatFabric have discovered a new strain of Android malware that comes with a wide array of features besides allowing a trojan malware called 'Alien' to steal credentials from 226 Android apps.
As per the researchers, the new trojan has been active since early 2020. They found that trojan has been offered as a Malware-as-a-Service (MaaS)—lease of software and hardware for carrying out cyberattacks—offering an underground hacking forum. The report published by ThreatFabric has revealed that Alien malware was based on the source code of a malware gang, known as Cerberus.

The New Malware: Alien
As per the security researchers, Cerberus, which was an active Maas till 2019, failed this year because Google's security team found a way to track and then clean malware-infected Android devices. But the researchers said that even if the Alien malware was based on the older Cerberus version, it is more advanced than Cerberus and dangerous.
The malware is a new generation of Android banking trojans that includes integrated remote-access features into the codebases and it makes the Alien malware a more dangerous creation to get infected with. The researchers noted that the new malware can show fake login screens on victims' devices, and it can collect passwords for various apps and services. The malware is also capable of allowing hackers to gain access to a device and use those credentials or to perform other cyber operations.
Features of Alien Malware
- Overlaying: Dynamic (Local injects obtained from C2)
- Keylogging
- Remote access
- SMS harvesting: SMS listing
- SMS harvesting: SMS forwarding
- Device info collection
- Contact list collection
- Application listing
- Location collection
- Overlaying: Targets list update
- SMS: Sending
- Calls: USSD request making
- Calls: Call forwarding
- Remote actions: App installing
- Remote actions: App starting
- Remote actions: App removal
- Remote actions: Showing arbitrary web pages
- Remote actions: Screen-locking
- Notifications: Push notifications
- C2 Resilience: Auxiliary C2 list
- Self-protection: Hiding the App icon
- Self-protection: Preventing removal
- Self-protection: Emulation-detection
- Architecture: Modular
The report also said that the developers behind Alien malware have a "particular interest in the usual set of most targeted countries, such as but not limited to Spain, Turkey, Germany, US, Italy, France, Poland, Australia, and the UK."
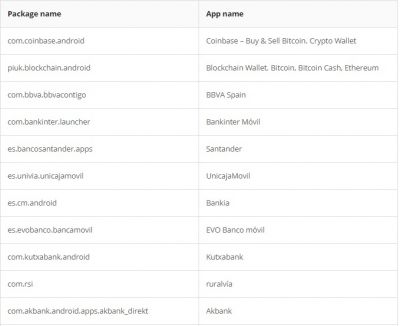
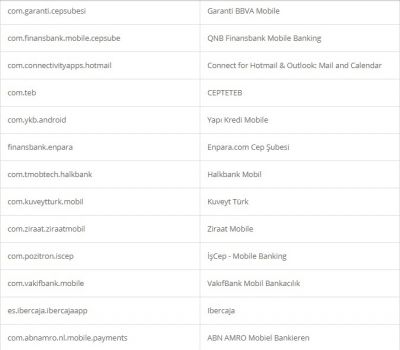
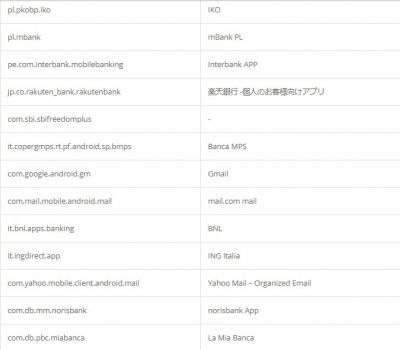
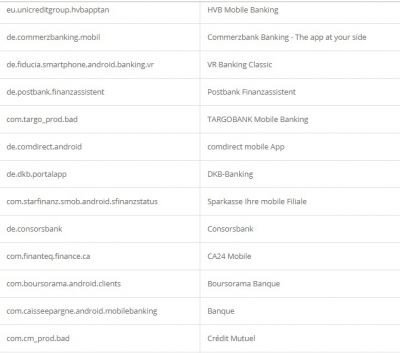
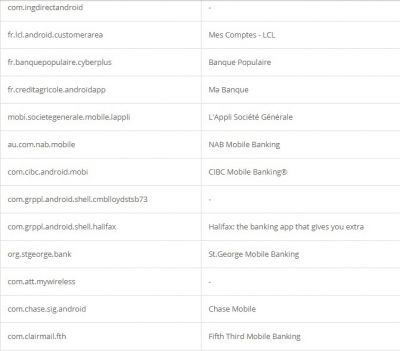
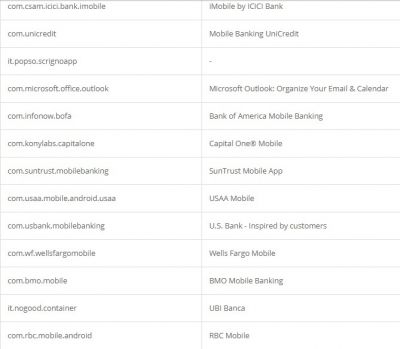
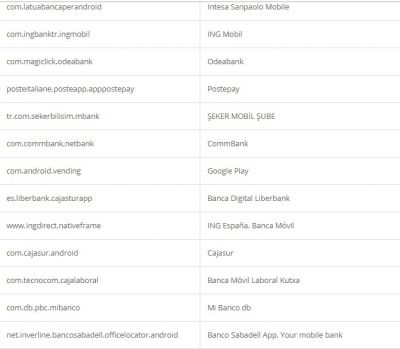
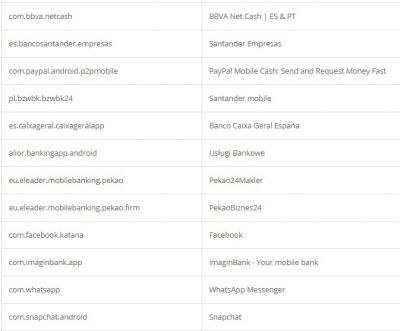
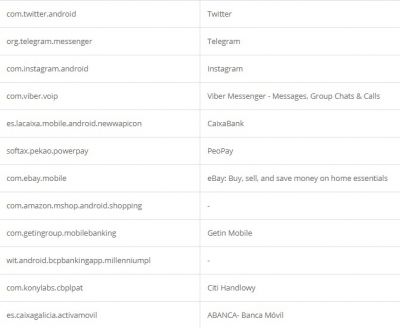
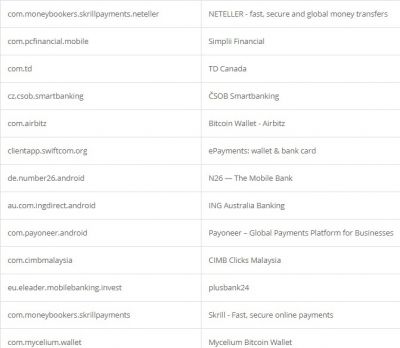
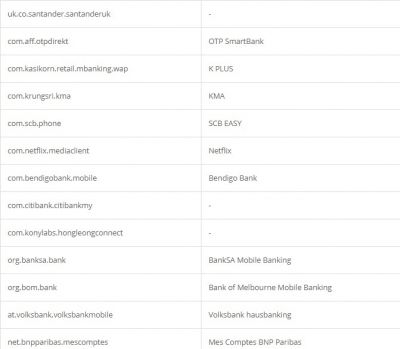
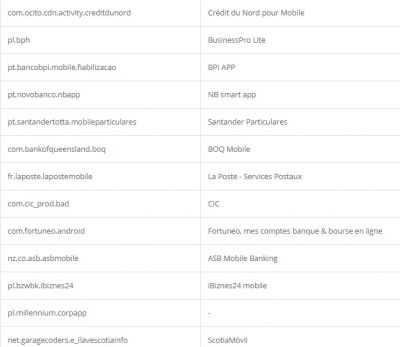
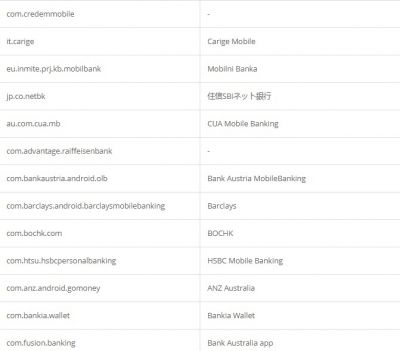
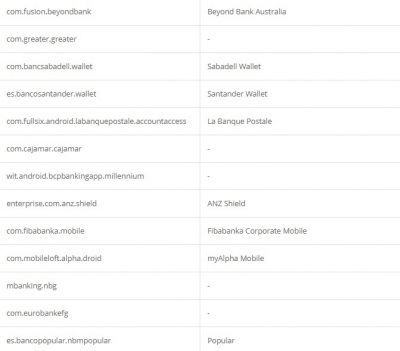
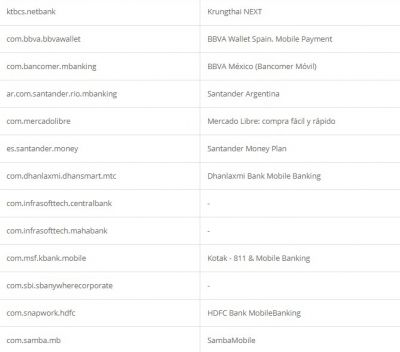
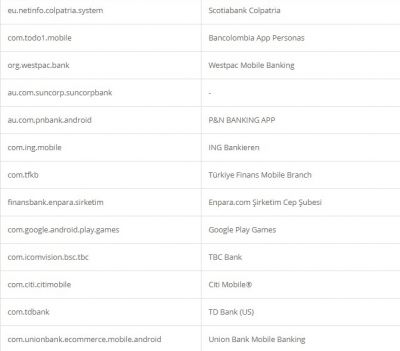
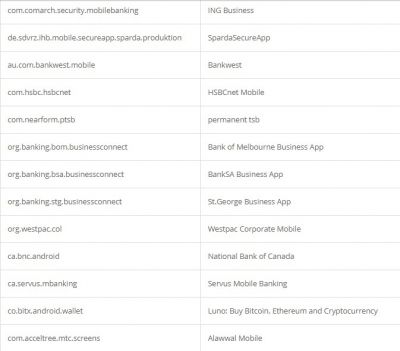
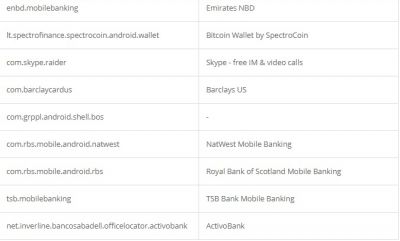
According to researchers, like other Trojan malware, these features of Alien are mostly used for fraud-related operations. It was also found that the malware had support for featuring fake login pages for 226 other Android apps. It has also targeted apps like email, social media, messaging, and cryptocurrency apps that include Twitter, Facebook, Telegram, Gmail, WhatsApp, and more. Here is the credential theft target list: