From the health sector to business, this is one of the most challenging situations which the world is facing due to the Coronavirus outbreak. While the disease has spread to 30 countries now, at least 2,004 people in mainland China have died from the Covid-19. Meanwhile, hackers around the world have found the Coronavirus serving them as an enabler for their malicious activities.
The malware named after Coronavirus
Earlier it was revealed that Kaspersky and IBM X-Force security researchers have found a series of malware campaigns that are using the coronavirus as a hook, while the health crisis in China has reached an emergency status forcing authorities and organizations to impose conveyance barricades.
Security company Check Point's Global Threat Index for January 2020 has shown that the malware has started to spread. As per the report, several spam campaigns thematically linked to the global epidemic have been found since the outbreak of the dangerous Coronavirus in Wuhan, China.
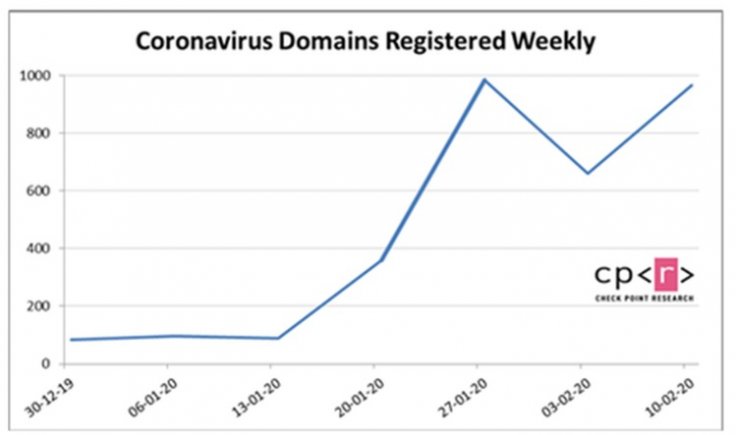
What is in the threat report?
The researchers at Check Point have noticed that an elevated number of new websites registered over the months of January and February with domain names related to the virus. They believe that these sites would be used to conduct phishing activities.
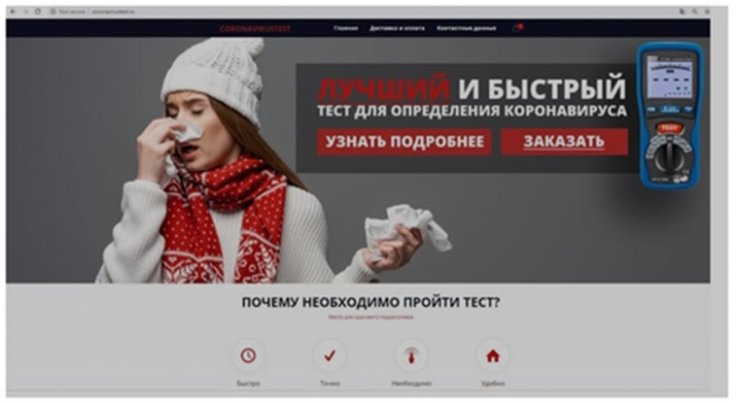
It should be mentioned that the report showed one example registered in Russia from February 11 which is vaccinecovid-19.com. The site claims to sell a "detection test" for the Coronavirus, and keeps publishing "news" stories and "heat maps" of the virus spread.
As per the Check Point researchers, the most prominent coronavirus-themed campaign has been targeting Japan via email and distributing Emotet, which is a type of Trojan malware. In this case, the Trojan works by posing as a disability welfare service provider and reporting where the virus has spread in Japan. It also points the malware victims to a malicious email attachment, which will allow the malware to be downloaded if they open it.
How to safeguard from this malware campaign?
Check Point has advised people not to click on such promotional links in email from any source. They are advised to avoid lookalike domains and unfamiliar email senders, in such cases a recipient can also look for check for spelling errors and weird formatting. People should not entertain any emails claiming special offers, such as "an exclusive cure for Coronavirus for $150."









