Among thousands of malwares, the InterPlanetary Storm (IPStorm) that was first uncovered in 2019 was considered one of its kind, targeting Windows systems. While the malware had unique features, some cybersecurity experts thought it would eventually disappear without a clear purpose. But that has now proved wrong. IPStorm has evolved into new variants that can not only target Windows systems but also Macs, Linux, Android and devices that run ARM architecture.
While the clear purpose of the malware is still unknown, the malware is now creating a botnet, infecting over 13,500 systems in 84 countries. Among them, it is prevalent in Hong Kong, South Korea and Taiwan. Cybersecurity researchers at Barracuda Networks believe the malware is creating backdoors for future DDoS (distributed denial of service) attacks and mining cryptocurrency.

Journey of IPStorm
IPStorm was first detected in May 2019 by researchers at Anomali. It was developed to target systems that ran the Windows operating system. However, the spread was limited only to a little over 3,000. It was unique at that time because it was written in Go programming language which was not very common those days. However, today, Go malware is pretty common.
The other feature was that it used InterPlanetary File System (IPFS) p2p network and libp2p implementation — a Python-based networking stack that allows users to develop peer-to-peer (P2P) applications — to communicate with each other, thus getting its name.
But in June 2020, Bitdefender noticed a variant of IPStorm malware that was infecting IoT devices (smart devices) like TVs that ran on Android OS and Linux based systems. Now, it has been confirmed by Barracuda in another report.
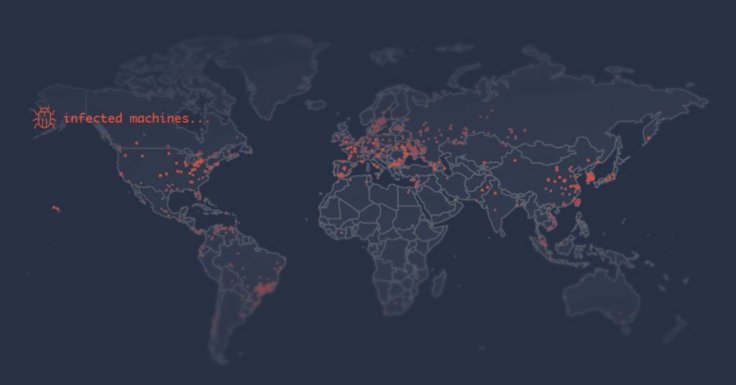
How Does It Spread?
Researchers believe that the malware is spread using brute force attacks on devices with Secure Shell (SSH). It is a remote administration network protocol that enables users to operate and modify servers remotely. As per Barracuda, IPStorm infects Android systems through exposed ADB (Android Debug Bridge) port while it uses dictionary attacks against SSH servers to identify usernames and passwords to infect systems that run Mac and Linux.
"The malware detects the CPU architecture and running OS of its victims, and it can run on ARM-based machines, an architecture that is quite common with routers and other IoT devices," researchers at Barracuda said. It means that smart home devices are vulnerable to such attacks.
Once IPStorm infects a device, it starts communicating with the command and control (C2C) server to identifying itself as a part of the botnet. According to researchers, the malware stays in the system and does not steal any files. Rather, it hides and updates once the system restarts and then spreads to other nodes of a network.
What Is the Purpose of IPStorm?
The clear goal of IPStorm is still unclear but as it creates a backdoor in the infected system and can communicate with each other, it is likely that it can be used for sophisticated DDoS attacks. With its download capability, it can also install a cryptocurrency mining app but researchers haven't uncovered any.
However, Intezar, a cybersecurity research firm, believes the malware is being used for advertising and gaming fraud. They noticed a spike in traffic in popular gaming store Steam's API. Steam is a common target for hackers because of its huge userbase.
"We noticed IPStorm generates a large amount of traffic to Steam's API, querying data pertaining to various Steam users and using multiple valid API keys. We suspect these are stolen accounts that are being monitored as part of a fake trade scam," Intezar researchers said.
Another potential purpose is advertising fraud. Intezar revealed that IPStorm generates requests that mimic fake advertisement clicks for pornographic sites. "The malware crawls through different predefined sites, searches for advertisement iframes, and imitates a user 'click' by browsing through the iframes," they added.
For now, what you can do to secure your system from IPStorm is to properly configure SSH servers. Barracuda researchers advise the use of keys instead of passwords.









