Cybersecurity researchers have found a new malware that has been infecting thousands of Android and iOS devices. The malware, designed to spy on victims' phones, can steal private data, including photos, GPS location, SMS, contacts and even unique device information.
Named Goontact, the spyware mainly infects devices in countries where people speak Mandarin like China, Singapore besides Japan, South Korea, Thailand and Vietnam. The malware is being distributed through third-party websites that promote free dating and instant messaging apps, according to a report from Lookout, a cybersecurity research firm.
"The spyware targets users of illicit sites, typically offering escort services and steals personal information from their mobile device. The types of sites used to distribute these malicious apps and the information exfiltrated suggests that the ultimate goal is extortion or blackmail," Lookout researchers said in a blog post.

'Sextortion Campaign'
The idea behind the malware is to extort money by stealing information related to booking escort services and compromising photographs. Once a Goontact-laced app is downloaded, it will have access to external storage, GPS, contacts, messaging and device information. Hence, if a victim has any compromising picture on the mobile device, the malware will be able to send it to a remote server.
According to the researchers, the actors lure victims to shady websites for connecting with women. However, to initiate conversation, the users will need to have instant messaging apps like KakaoTalk or Telegram. The threat actors advertise instant messaging IDs on such websites. Once the user starts conversing on those apps, the individual will be asked to side-load or download another app laced with Goontact malware. In reality, the user will converse with the malware operators.
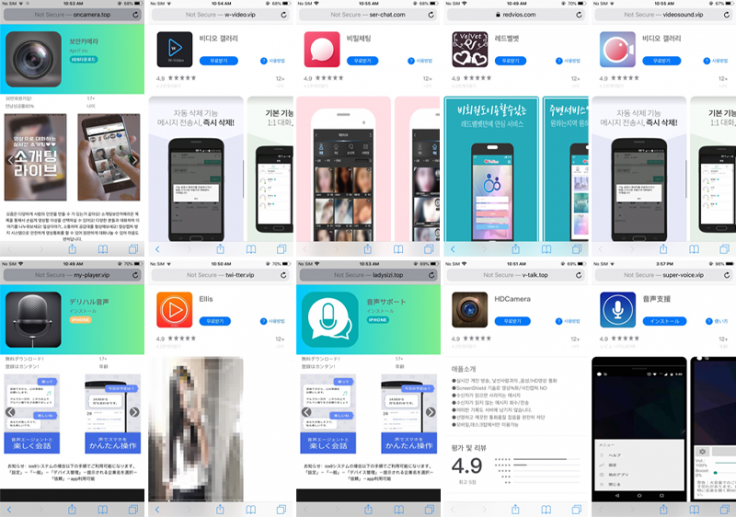
"The mobile applications in question appears to have no real user functionality, except to steal the victim's address book, which is then used by the attacker ultimately to extort the target for monetary gain," the researcher said.
Similarities with Past Campaign
This is not the first time that a group is managing a sextortion campaign. In 2015, Trend Micro, another cybersecurity research firm, revealed that a group was operating in East Asia with similar motives. However, the malware in 2015 was limited to Android, but the Goontact spyware has spread its wings to iOS.
While Lookout researchers didn't find any links between the two scams, it is possible that the same criminal group is behind both malwares. According to researchers, the sextortion campaign targeting mobile devices has been active since 2013 but Goontact malware is rather new and has been operating since 2018.



Lookout researchers have informed both Google and Apple about the threat and have been collaborating to protect Android and iOS users. "Apple has revoked the enterprise certificates used to sign the apps and, as a result, the apps will stop working on devices. Play Protect will notify a user if any Goontact Android samples are installed on their device," Apurva Kumar, Staff Security Intelligence Engineer at Lookout, told ZDNet.








