
A new variant of a malicious software has recently been found out by experts hiding under different apps in Android smartphones. The identified malware is a Trojan reportedly aiming to steal victims' banking information.
Anti-virus software company Kaspersky Lab reported on Thursday that a new variant of the Faketoken Trojan it called "Faketoken.q" has been discovered hiding under various apps. The strain has attacked Android Pay, Google Play Store, some flight and hotel-booking apps, traffic ticketing apps, taxi-booking apps and a number of mobile banking apps.
Kaspersky Lab's Alex Drozhzin says the Faketoken Trojan is an old malware that has been morphing into different strains over the last few years.
How Faketoken.q attacks
Faketoken.q gains entry to smartphones through bulk SMS messages containing an instruction to download some image. Once the user downloads it, certain modules will start to install and a shortcut for the Trojan will create which covertly monitors the activities in the phone's entire system.
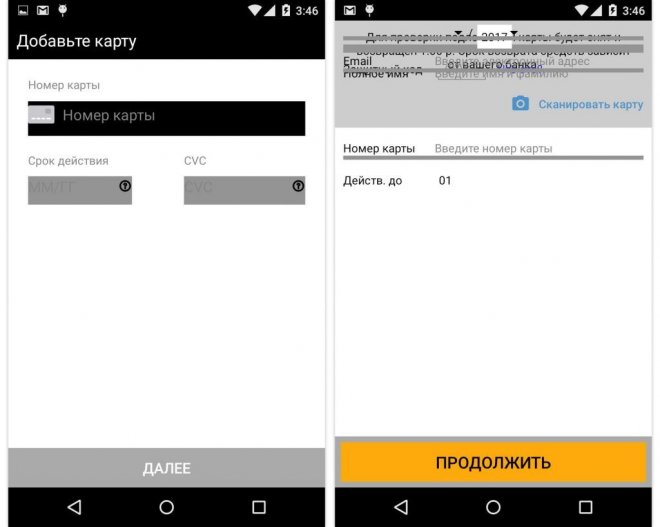
It can detect calls and record it and check which apps are being used. Once it senses that an app is launched, Faketoken.q sits on top of the app with its own screen in an overlay. Users will not be able to clearly notice it since the Trojan can copy the colours of the original app's interface.
In the same window, Faketoken.q prompts the user to input the credit card number as well as the card's three-digit verification code. The Trojan will then use another trick to siphon off money from the card to prevent suspicion.
Faketoken.q intercepts incoming SMS messages to prevent the user from receiving it. Criminals behind it will then extract passwords for payment confirmation from those messages.
How to avoid Faketoken.q attacks
Faketoken.q roots trace back to Russia. However, Drozhzin notes that cybercriminals outside the country are likely to copy this method so it will not be impossible to see a similar modus in other parts of the world.
To avoid such attack, users have to tweak their phone's security settings by preventing installation of software from unknown sources. For Android phone owners, go to Settings > Security > uncheck Unknown sources.
It is also important to examine which app requests to grant permissions to. Google Play can also be a hotspot for Trojans so it pays to be cautious with app permissions.









