The U.S. Department of Justice indicted a pair of Chinese nationals on Tuesday, July 21 over their role in what it called a decade-long cyber espionage campaign, targeting U.S. defence contractors, high-end manufacturing and solar energy companies and now Coronavirus research, with several victims falling prey to them worldwide.
As per the U.S. authorities, these two Chinese hackers, Li Xiaoyu and Dong Jiazhi had stolen terabytes of weapons designs, software source code, drug information, and personal data from several targets. It was also claimed that these two threat actors had previously stolen information about other Chinese intelligence targets like human rights activists and this year at the behest of the Ministry of State Security spy service, they shifted the focus to acquire Coronavirus vaccine research.

The U.S. officials said that Xiaoyu and Jiazhi were contractors for China's Ministry of State Security (MSS), which is a counterpart of the Central Intelligence Agency.
Chinese Hackers
The indictment comes close on the heels of the Trump's administration stepping up its criticism of China, for Beijing's failure to contain the spread of SARS-CoV-2 and theft of secrets. It also coincided with the U.S. allies pointing out Russia of trying to steal information on Coronavirus vaccine development.
After the indictment, John Demers, the U.S. Assistant Attorney General for National Security said at a virtual press conference that the hacking showed Beijing wanted to "turn a blind eye to prolific criminal hackers operating within its borders."
He further said China has now taken its place, alongside Iran, Russia, and North Korea, in that "shameful club of nations that provide a safe haven for cybercriminals in exchange for those criminals being on call for the benefit of the state."
The Indictment
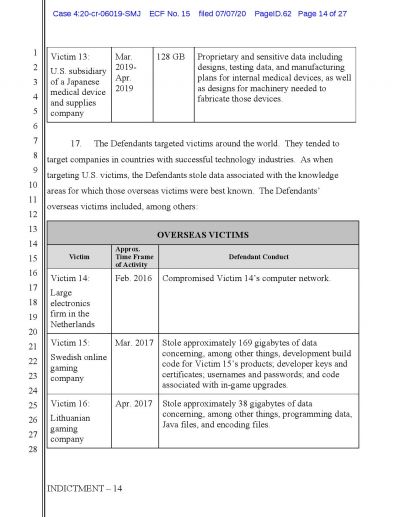
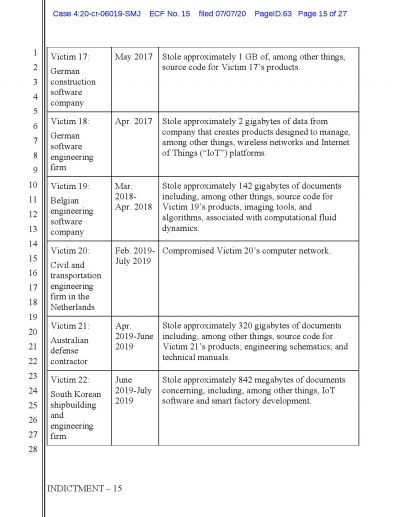
While the names of targeted companies or individuals are yet to be revealed, the U.S. Attorney William Hyslop said there are "hundreds and hundreds of victims in the United States and worldwide".

As per the U.S. officials, the probe was triggered when in 2015 the cybercriminals broke into a network belonging to the Hanford Site, which is a decommissioned nuclear production complex operated by the U.S. federal government on the Columbia River in Washington State.
FBI Special Agent Raymond Duda, who heads the agency's Seattle field office said that Xiaoyu and Jiazhi were "one of the most prolific groups of hackers we've investigated."
The prosecutors said that the MSS had supplied the cybercriminals with information into critical software vulnerabilities to infiltrate the targets and collect intelligence related data. They also mentioned that these targets included protesters in Hong Kong, the office of the Dalai Lama, and a Chinese Christian non-profit.
After the novel Coronavirus hit the world and the COVID-19 started to make its way from China to other countries, the Chinese hackers began their new mission. The indictment claimed that the threat actors were trying to steal Coronavirus vaccine research from an unnamed Massachusetts biotech firm. In February, the pair tried to find vulnerabilities in the networks of a California biotech firm that had announced it was researching on Coronavirus drugs.
The indictment also added that in some cases, the threat actors tried to extort money from companies, for example, in 2017, Xiaoyu threatened to publish the source code of a Massachusetts software company if it did not pay him $15,000 in cryptocurrency.
While the indictment named only the two suspects as of now, unlike the larger group of Russian cybercriminals, accused of seeking vaccine data, the U.S. Justice Department portrayed Xiaoyu and Jiazhi's work as far-reaching and long-running, going back to at least 2009.
However, as of now, it is unclear whether they had stolen anything or not, but an expert claimed that the allegations showed the "extremely high value" that governments such as China placed on SARS-CoV-2 related research.