
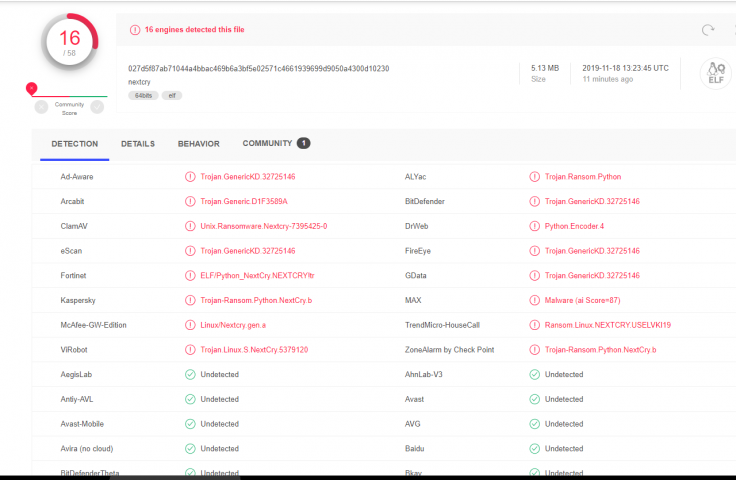
This year we saw a resurgence of ransomware attacks around the world, and it is supposed to be more gruesome with the arrival of a new ransomware called NextCry. The malware was spotted by the security experts lately, infecting Linux servers in the wild.
The potential targets of this new ransomware are the users of NextCloud file sync and share service. As per reports, NextCry had been compiled in a Linux ELF binary using the PyInstaller application and is a python file.
Once the ransomware infects the victim's machine, it encrypts all the files with appending the word 'nextcry'. Later it finds out backups and encrypts it as well to lock down the entire system. Once compromised, the author of NextCry ransomware demands a ransom worth BTC 0.025, which translates to 210 USD roughly at the time of filing this report.
The ransomware drops a note while locking down the systems, which reads as "YOU HAVE BEEN HACKED YOUR FILES HAVE BEEN ENCRYPTED USING A STRONG AES-256 ALGORITHM – SEND 0.025 BTC TO THE FOLLOWING WALLET wallet address AND AFTER PAY CONTACT their email TO RECOVER THE KEY NECESSARY TO DECRYPT YOUR FILES."
NextCry has already detected by McAfee-GW-edition, Kaspersky, eScan, ClamAV Fortinet, Arcabit and VirRobot anti-virus engines. Rest of the cybersecurity solution providers are yet to recognize or come up with a solution to detect and mitigate the system.
In other news, Mexico based Oil Company Pemex fell prey to a ransomware attack. Through a tweet, the Pemex official handle accepted the breach but denied any damage on its network. The company asserted, all of its industrial systems or safety gear remained untouched by the ransomware attack.









