Google's two-factor-authentication or 2FA offers additional security to accounts. But an Iranian hackers' group might have found a way to steal that code as well. As per reports, the hackers have developed an Android malware that can intercept text messages starting with 'G-' Google's 2FA SMS.
Besides the Android malware, the group, nicknamed, Rampant Kitten, has also developed other tools to steal personal data from Windows devices and Telegram accounts. The malware has been specifically used against Iranian resistance movements, anti-regime organizations and Iranian minorities. However, with the U.S. intelligence agencies warning against growing cybersecurity threats from Iranian hackers, the same malware can be used in other countries including the U.S.

"According to the evidence, we gathered, the threat actors, who appear to be operating from Iran, take advantage of multiple attack vectors to spy on their victims, attacking victims' personal computers and mobile devices," cybersecurity research firm Check Point, which identified the malware, said.
Android Malware
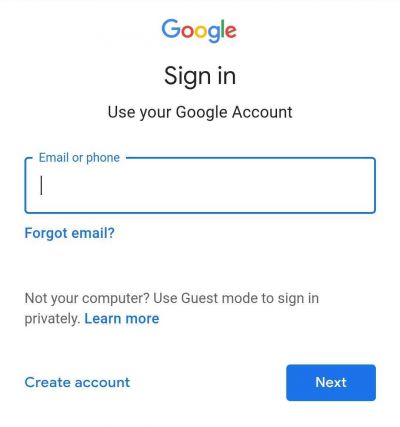
The Android malware is disguised in apps that have backdoors. Once installed, it can then steal users' contacts, use the microphone to silently record the victim and also copy text messages (SMS). As per Check Point's research, Rampant Kitten would then show the victim a Google phishing page to record usernames and passwords. If 2FA is enabled, the malware will automatically read messages that start with G- string and send it to the hackers without the user knowing.
Researchers found an Android app that helps Iranian citizens get a Swedish driver's license among such malicious apps. But there could be others. When the app is launched, the user needs to log in with an email account that opens in Android's WebView. To steal the credentials, hackers use Android's Javascript Interface that retrieves the information from the input fields.
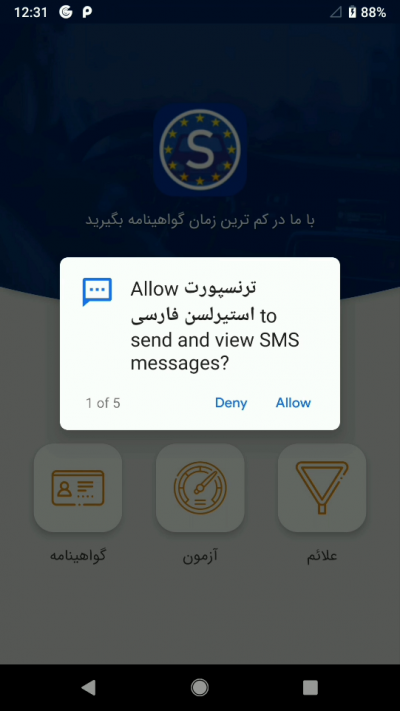

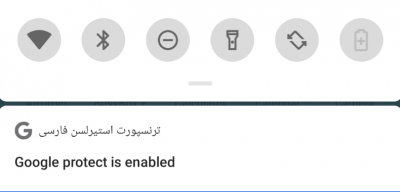
As the malware also records voices through silently turning on the microphone, it needs to run in the background. However, Android informs the user of any ongoing background activity by providing a notification that can not be ignored. Thus, the malware displays a fake notification that says "Google protect is enabled" to circumvent the issue.
Windows Strain
The same malware has a version to target Windows users as well. While it is not known which payload delivery the hackers particularly used, Check Point said that one potential method could be a phishing software. It promises to increase the number of members in Telegram channels.
The software comes password-protected archive that contains one of the malware variants, Check Point said. Once the archive file is extracted, it can access the desktop's files, Telegram Desktop and also KeePass, a password manager.

Besides that, the malware is also capable of finding any files with .txt, .csv, .kdbx, .xls, .xlsx, .ppt and .pptx extensions. The malware encodes the files to base64 and then sends them to the hackers' FTP server. The U.S. Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) jointly with the FBI had also warned of similar attacks earlier this week.
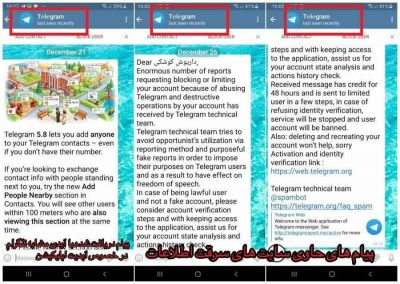
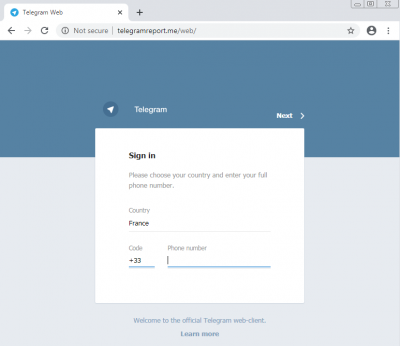
The same malware is also run through a phishing scam on Telegram. The social media app's users get a notification from a channel that disguises as the official Telegram's channel. It asks the user to login to his account to verify through a phishing page that looks similar to Telegram. Once the user logs in, it captures the details of Telegram credentials.