The coronavirus pandemic has changed many things around us, and work is the most critical aspect of it. Following lockdowns across the globe, both public and private enterprises have been compelled to make at least 50-70 per cent of employees to work from home. This has increased the number of vulnerable devices connected to the enterprise network, which could lead to a cyber attack.
WfH - the new challenge for CISOs
Cybersecurity solution provider Sepio Systems has flagged that even though CISOs are adopting more robust security strategies to strengthen enterprise security, the innumerable vulnerable devices used by remote workers make them riskier.
Unrecognised accessories
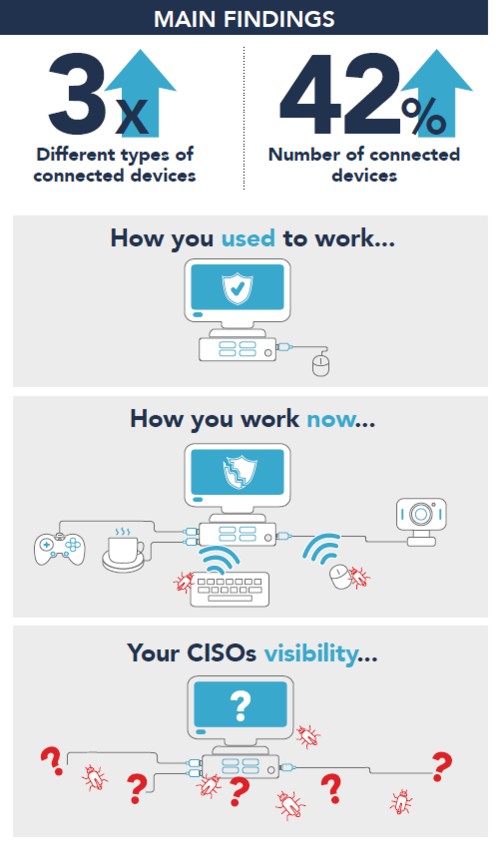
In its latest findings from its proprietary cloud service, Sepio Systems has experienced a massive surge of 300 per cent in the number of new connected devices attached to the enterprise network and a 42 per cent increase in the number of connected devices. The company has also noticed an almost threefold increase in devices from unknown vendors. Accessories like keyboards, mice and USB charging cables are found to be from unrecognised and cheap vendors. They don't follow any security standard and thus make the network vulnerable to hack.
"We now see almost three times the number of different device vendors – many of which are no-brand unrecognized cheap devices that are not common in the enterprise environment," Sepio Systems noted. "This significant rise is attributed to the fact that employees are connecting their existing home peripheral to their endpoints."
Why vulnerable
Sepio Systems says that such hardware components could be connected to microcomputers such as the Raspberry Pi or Audrino and exploit them to deliver malicious payloads. A hacker can execute attacks such as man-in-the-middle (MiTM), distributed denial of service (DDoS), keylogging or data breaches. The US-based cybersecurity solution provider has also claimed that such attacks can be executed in a fraction of a second by gaining access to an organisation's network via any vulnerable device and execute attacks remotely.










