In the last few years, cybercriminals have adopted new techniques to target victims. While some of them are more complicated exploitation of vulnerabilities, some methods still involve good old phishing. Despite increasing awareness, the latter remains the most effective tool. Phishing scams generally involve luring victims into clicking on a malicious link for a ransomware attack or credential harvesting. In a recent campaign, hackers were able to get away with the Facebook login credentials of over 615,000 users.
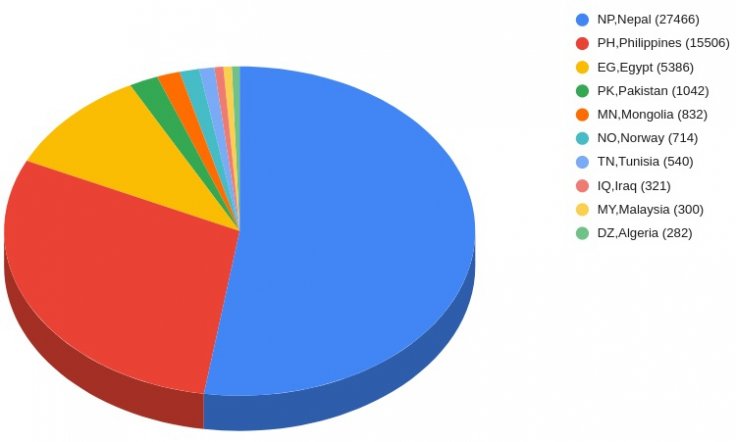
In the recent campaign, cybersecurity research firm ThreatNix said, the hackers redirected the users who clicked on the ads to a GitHub phishing page that resembled Facebook's landing page. The campaign was spotted in Asian countries such as Malaysia, Philippines, Nepal, Pakistan, besides Egypt amongst others.

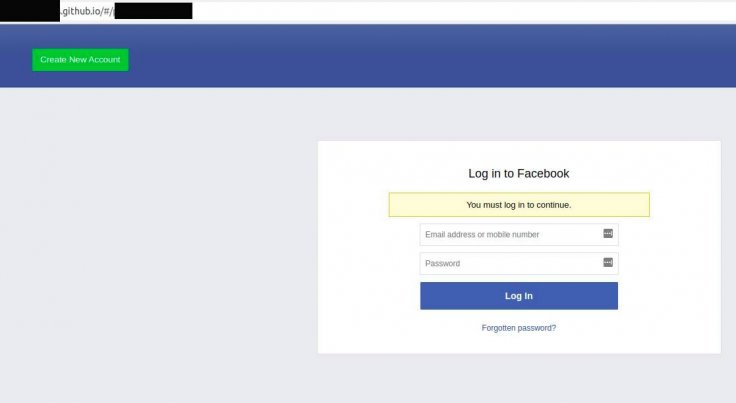
"The campaign is using localized Facebook posts and pages spoofing legitimate entities and targeted ads for specific countries. Links within these posts then redirected to a static GitHub page website that contained a login panel for Facebook. All these static GitHub pages forwarded the phished credentials to two endpoints one to a Firestore database and another to a domain owned by the phishing group," the researchers explained.
Sophisticated Attack
The hackers created localized Facebook ads from legitimate companies. For example, the researchers found an ad from Nepal Telecom offering 3GB mobile data for free. As the users clicked on the provided link, they were redirected to a page on GitHub where they needed to enter the Facebook login details. Such localized ads were found in Pakistan and the Philippines.
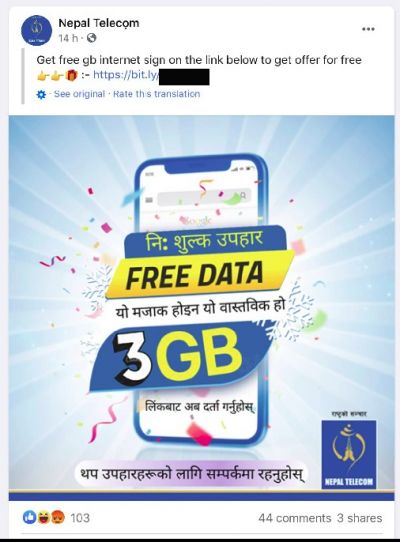

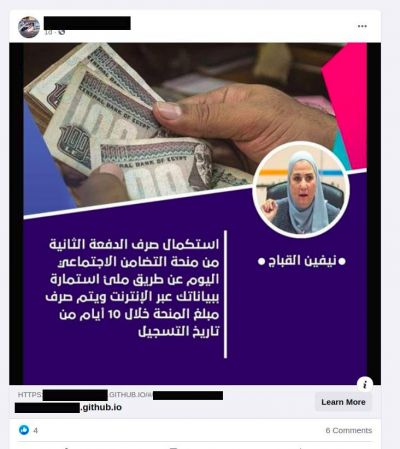

To evade Facebook's detection, they used shortened URLs that initially redirected to a benign page. But once the ad was approved, the shortened URLs were modified to take the user to the phishing page. As per researchers, the hackers used nearly 500 GitHub repositories that contained phishing pages. The earliest page was created five months ago while most of them were abandoned in the last few months.
"Following some digging we were able to gain access to those phished credentials. At the time of writing this post, there appear to be more than 615,000 entries and the list is growing at a rapid pace of more than 100 entries per minute," the researchers said.
The harvested credentials included mobile number, Facebook login details, email ID, password, name and IP address. However, if a user had their Facebook profile updated with home address and payment information (such as credit card number or so), it is likely that hackers got their hands on them too.
Similar Campaign
The Nepalese cybersecurity research firm has notified Facebook and other relevant authorities about the campaign and together they are working on taking down the ads. However, this is not the first time Facebook ads have been abused to harvest credentials.
In October, Facebook's own security team revealed that hackers swindled over $4 million from users with the SilentFade malware attack. The localized ads were used to sell fake products related to weight-loss, diet pills, sexual health besides handbags, shoes among many others. Facebook's security researchers said that the malware was a new variant of SuperCPA which was linked to a Chinese hackers' group. However, as for the latest campaign, researchers haven't attributed the phishing attack to any group yet.