In the last few years, strengthening cybersecurity has become a nightmare for companies. Hence, many of them look forward to contributions from cybersecurity researchers — independent and organization both. But now, a new study by Google has revealed that hackers, especially the North Koreans, have shifted their focus on those researchers.
Security researchers play an important role in identifying vulnerabilities before hackers do and notify the companies so that they could fix them. These ethical hackers are often targeted by malicious actors. That way, they can malign their credibility and also get insight into valuable information. As per Google, such a campaign is ongoing by a North Korean Advanced Persistent Threat group (APT).

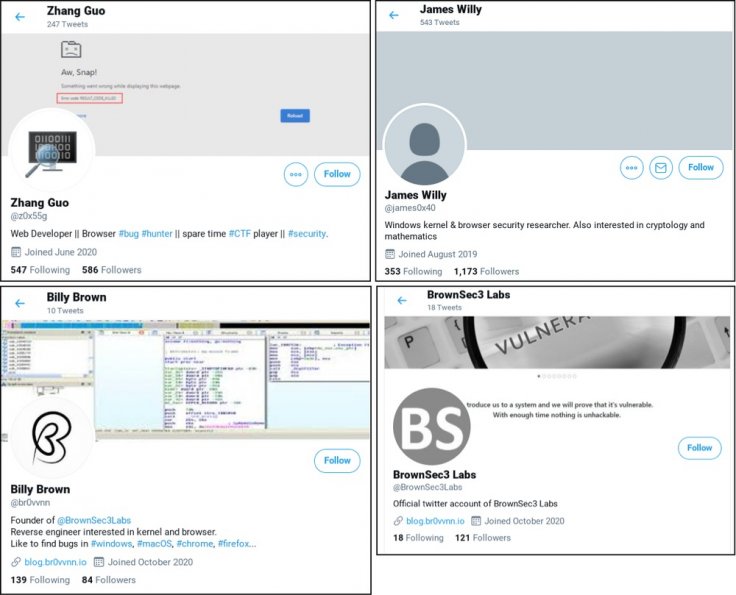
Those malicious actors are trying to build credibility and rapport with security researchers by creating multiple research blogs and Twitter accounts. While many such blogs contain legitimate research on vulnerabilities, most are analysis on publicly disclosed threats and guest posts. As per Google, most of the guests had been tricked into believing that their research was going to be published on a legitimate site.
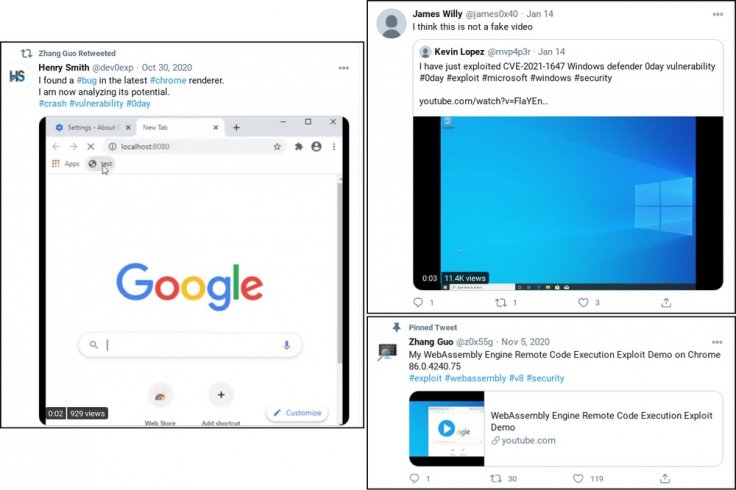
"They've used these Twitter profiles for posting links to their blog, posting videos of their claimed exploits and for amplifying and retweeting posts from other accounts that they control," security researcher, Adam Weidemann, from Google's Threat Analysis Group said in a post. It added that at least one video posted on YouTube turned out to be a fake one that did not exploit the vulnerability.
How Do They Target Researchers?
After amplifying their works and building credibility through Twitter, the North Korean hackers approach cybersecurity researchers to collaborate on any vulnerability research project. If any researcher agrees, the hackers then send a Visual Studio project. It includes the source code to exploit the vulnerability but also contains a DLL with disguised custom malware that helps the hackers connect to a command-and-control center.
Dirk Schrader from the New Net Technologies Ltd, a cybersecurity and compliance software company, told SiliconANGLLE that it is a broader attempt to get insights into the vulnerabilities that the researchers are working on.
"If it would have been more successful — we don't know yet how many researchers actually got caught — the APT group likely would have garnered valuable info and would have provided itself a head start on exploiting the vulnerabilities discovered by those researchers," said Schrader, who is also the Global Vice President of the company.
With early access and advanced insight into the research, hackers can use the method to exploit the vulnerability before it is fixed. Generally, once a researcher informs about a security flaw, the company gets a 90-day period to fix it. The researcher can publicly disclose the vulnerability only after that period. But at times, more complex fixes can take more than that and hackers try to exploit that within 90 days.
"That is why it is critical to learn as much as possible about this social engineering attempt because it will serve as a template for others, similar to the SolarWinds attack," Schrader said.
Victims Share Experience
While it is difficult for cybersecurity researchers to come forward and reveal they were duped, many shared their experiences on Twitter. A researcher, who goes by the name Will Bushido, said he was targeted by a Twitter handle named "z0x55g". He was asked about his research on Windows kernel 0-Day vulnerability.
Another security researcher, Richard Johnson, was also a victim of the attack. But since he ran the program in VM (virtual machine), it did not impact his work. There were many such instances.









