Hackers are targeting Microsoft SQL (MSSQL) servers to install crypto-mining malware. So far, thousands of MSSQL databases have been infected as per Chinese technology giant Tencent's cybersecurity wing.
The Chinese company named the malware MrbMiner after discovering that hackers used one of the domains after the same name. According to Tencent, hackers scan through the internet for MSSQL servers and use brute-force attacks to gain access. Through this process, hackers target the admin account and try to log in with a large number of possible weak passwords.

Crypto Mining Malware
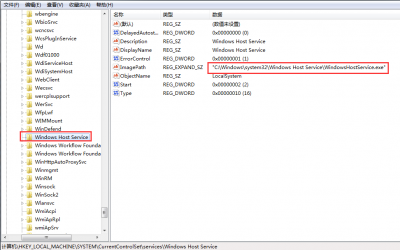
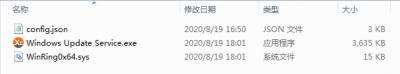
After gaining access, hackers then download assm.exe which is written in C# beside two others installerservice.exe and PowerShellInstaller.exe. The downloaders install a system service that runs in the background and continues to gather system information including CPU type, CPU number and .Net version information. It also blocks the Windows upgrade service, creates a reboot mechanism and adds a backdoor for future access. The company said that hackers used the username "Default" and "@fg125kjnhn987" password for future access.
Once that is done, the malware then communicates with the command and control server (C2 server) to download an app that abuses the machine resources to mine Monero (XMR) cryptocurrency as per Tencent. The mined crypto is then stored in accounts created by the hackers.
"MrbMiner mining Trojan will carefully hide itself to avoid being discovered by the administrator. The Trojan will monitor the Task Manager process. When the user starts the Task Manager process to view the system, the mining process will immediately exit and delete related files," Tencent said in its report.
ARM and Linux Version Found
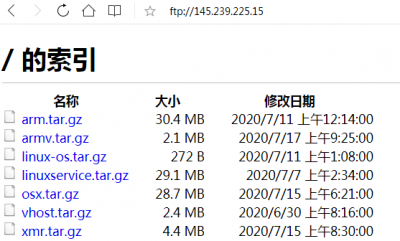
While the crypto mining malware specifically targeted MSSQL servers run on Windows, Tencent researchers also found versions of the trojan that were written to target ARM and Linux based servers. The associated mining accounts contained 3.38 XMR or little over $300 while the Windows-based servers had mined 7 XMR or (little over $630), ZDNet reported.
The network administrators can scan their MSSQL servers to block the backdoor account while they can also find traces of the malware in Windows registry files.

MSSQL servers are used all over the world by small to large companies for database management. However, most of the time, the popular database management solution has seen inadequate protection. Hence, hackers have tried different methods to exploit MSSQL vulnerabilities to gain access.
It is also not the first time that hackers have targeted MSSQL to mine cryptocurrencies. Last year, Kaspersky, an antivirus and security solution, discovered a similar malware that was targeting MSSQL servers. Named as Agent 1433, the remote access malware was used to gain access to the system and could disguise itself in the system without the administrator noticing. It utilized "jobs", a sequence of commands executed by SQL Server Agent that launches transactions and scripts, to make the malware secure in the system.









