From smartphones to earphones, speakers, fitness bands, smart devices, car keys, remote controls and game controllers, most of the everyday devices use Bluetooth technology. However, thanks to the widely distributed and adapted technology, it has often been targeted by hackers. Now, billions of devices are vulnerable to a newly discovered security flaw.
As Bluetooth technology improved, one of its biggest complaints was that it consumed excess energy. It was fixed through implementing Bluetooth Low Energy (BLE) protocol that was intended to reduce power consumption while keeping the connection active. It was introduced in the 4.0 version and since then billions of devices have implemented the protocol.
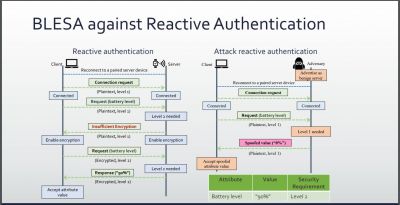
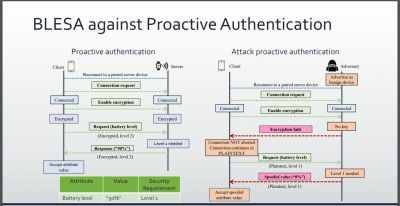
However, as per researchers at Purdue University, (U.S.), the BLE mode has a flaw that can be exploited by hackers. Dubbed as the Bluetooth Low Energy Spoofing Attack (BLESA), seven researchers analyzed the "reconnection process" and found that authentication could be evaded.
Reconnection Flaw
During the pairing process, two Bluetooth devices authenticate each other by generating cryptographic keys for data exchange. Once one of the devices move out of the range, it then again reestablishes the connection. But Purdue researchers found that the reconnection process was not strong enough. The flaw was mainly in the BLE software implementation. During the reconnection process, authentication was left optional instead of making it mandatory for stronger security meaning that it could be bypassed.
"To ease its adoption, BLE requires limited or no user interaction to establish a connection between two devices. Unfortunately, this simplicity is the root cause of several security issues," researchers wrote in the paper.
Those security flaws could be exploited by hackers for a BLESA. An attacker can eavesdrop and spoof the data. Another potential abuse could be MAC address cloning. As the BLE advertising packets are sent in plain text, an attacker can mimic the server by sending the "same packets and cloning its MAC address," according to the researchers. By doing so, the attacker can transmit spoofed advertising packets whenever the client starts a new session with the previously-paired server.
hackers can also distribute a denial-of-service bug that could make Bluetooth connection go offline. It would then trigger a reconnection to execute a BLESA, ZDNet reported.
Windows Unaffected
While a patch can fix the issue, not all devices are equipped to be updated, meaning those will remain vulnerable forever. Researchers found that Linux-based BlueZ, Android-based Fluoride and Apple's iOS BLE stack for IoT devices were especially susceptible to such BLES attacks. However, Windows is the only operating system that researchers found to be secure.

The researchers informed Apple and Google regarding the issue and the former said it had issued a fix in June (2020) through CVE-2020-9770. However, they said that "the recent Android BLE implementation (May 2020) in our tested device (Google Pixel XL running Android 10) was still vulnerable." Linux's BlueZ development team responded saying that it would fix the code with proper reconnection process.
Another major security flaw in Bluetooth was also discovered last week. Dubbed as "BLURtooth" vulnerability, hackers could bypass authentication keys within range to eavesdrop. It could also give an attacker access to other Bluetooth devices connected to the victim's device. All Bluetooth devices between 4.2 and 5.0 standards are vulnerable while the 5.1 version comes with a feature that can prevent such attacks.









