The infamous Russian hacker group Fancy Bear that is also known as APT28 and Strontium is targeting government agencies of NATO member countries. The group which was allegedly behind the hacks on Democratic National Convention in 2016 in the U.S., is now using sophisticated malware named Zebrocy Delphi to target government bodies and steal data.
First detected by QuoIntelligence in August 2020, the cybersecurity researchers at the company found the malware was disguised in the form of fake NATO training materials being sent to the target computers. On first look, it would seem that the training materials were legitimate but a closer look revealed the malicious intent.

NATO Training Materials
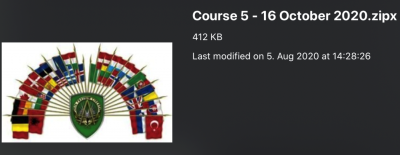
The course material distributed by APT28 contained "Course 5 – 16 October 2020.zipx". The file looks like an archived zip file containing NATO materials. When the researchers renamed the zip extension to .jpg, they found that it behaved exactly like an image file, showing the logo of the Supreme Headquarters Allied Powers Europe (SHAPE), NATO's Allied Command Operations (ACO) in Belgium. However, it was not what it seemed.
When researchers dug deep, they found the "zip file concatenated." "This technique works because JPEG files are parsed from the beginning of the file and some Zip implementations parse Zip files from the end of the file (since the index is located there) without looking at the signature in the front," researchers explained.

Evades Antivirus Detection
Through this technique, Fancy Bear hackers wanted to evade antivirus detection as the software would skip testing it mistaking it for an image (JPG/JPEG)) file. However, to decompress the file, one must use WinRAR. If the victim uses WinZip or any other decompression software, it would show an error message claiming that the file is corrupted.
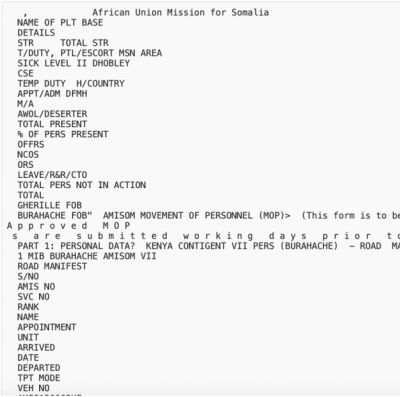
Once decompressed, two files are shown "Course 5 – 16 October 2020.exe" and "Course 5 – 16 October 2020.xls". The excel file, however, cannot be opened by Microsoft Excel as it shows corrupted. The researchers found that the file contained information about military personnel for an "African Union Mission for Somalia".
However, the target was to lure the victim into opening the other file which comes with a PDF icon and it contained the Zebrocy Delphi malware. If file extensions are not shown, the victim would unknowingly click on the PDF but it's an executable file (.exe) mistaking it for PDF with course material.

Once executed, the file drops the Zebrocy malware and creates a scheduled task to send the stolen data to a remote server. It also communicates with a command and control (C2) in France. As per BleepingComputer, Zebrocy malware can be used for multiple purposes. It can create and modify files, take screenshots and execute commands.
Azerbaijan Targeted
QuoIntelligence found that Azerbaijan had been targeted with malware. Although the country is not part of NATO, it cooperates with the alliance and takes part in training exercises. Researchers believe many other NATO countries might have been already targeted.
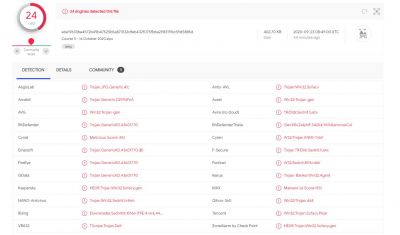
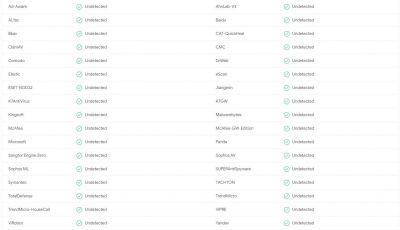
They also found similarities with ReconHell/BlackWater attack that they uncovered in August. Both the attacks use compressed Zebrocy malware and the course material to lure victims. Interestingly, both samples were uploaded by the same user in Azerbaijan. Researchers also found a copy of the malicious file uploaded to VirusTotal, an antivirus aggregator tool. It could avoid detection from Microsoft's antivirus tool and other popular detection software.









