As we have moved more towards an internet-connected ecosystem, smart home solutions have become prominent. From light bulbs to thermostats and more, everything is now at users' fingertips. But how secure is Internet of Things (IoT)? As per a cybersecurity research firm, millions of IoT devices are not secure and are vulnerable to hacking.
According to a report from Forescout Technologies, devices from around 150 manufacturers have security flaws. The products include smart plugs, routers, healthcare appliances and even industrial control systems. But most affected among them are smart cameras and temperature control systems at our homes.
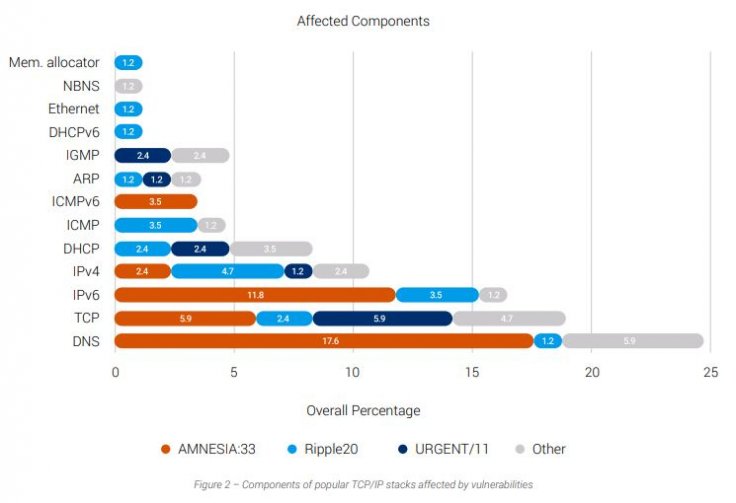
The report titled "Amnesia:33" highlighted the lack of attention to security and sloppy programming by developers. Researchers found 33 vulnerabilities that could affect different components of stacks including DNS, IPv6, IPv4, TCP, ICMP, LLMNR and mDNS while two other flaws could only impact 6LoWPAN wireless devices. Those vulnerabilities could lead to distributed denial of service attacks (DDoS), remote code execution attacks or even a complete takeover of the devices.
TCP/IP Stacks Vulnerabilities
During their investigation, researchers found four of seven TCP/IP stacks vulnerable – uIP, FNET, PicoTCP and Nut/Net. While Forescout didn't find any flaws in IwIP, CycloneTCP and uC/TCP-IP, there could still be issues. For some time now, security researchers have been warning about the vulnerabilities in crucial TCP/IP stacks that allow communication over the network.
"A security flaw in a TCP/IP stack can be extremely dangerous because the code in these components may be used to process every incoming network packet that reaches a device. This means that some vulnerabilities in a TCP/IP stack allow for a device to be exploited, even when it simply sits on a network without running a specific application," the report said.
Many of the problems were in Domain Name System (DNS) that translates domain names into IP addresses and includes mail servers. Forescout researchers said that due to DNS's complexity, it remained vulnerable.
Problem of Open-Source
The main problem behind vulnerabilities in TCP/IP stacks is its open-source nature. Most of the IoT manufacturers don't develop their own software completely. Instead, they depend on open-source stacks. In open-source programs, there is no particular developer who could fix an issue. Rather, volunteers take up the job to update or fix such vulnerabilities.
"It is difficult to assess the full impact of AMNESIA:33 because the vulnerable stacks are widely spread across diverse IoT, OT and IT devices in different verticals. They are highly modular and often incorporated in embedded components such as systems-on-a-chip (SoCs) that are later used by device manufacturers. For the same reasons, these vulnerabilities tend to be very hard to eradicate," Forescout researcher Daniel dos Santos explained.
Mitigation of Risks
As more and more people are working from home, hackers can target smart home devices to get into corporate networks through employees' computers. For example, if someone is using a vulnerable router to connect to the internet and accessing the office server, hackers can target the entire network.

Hence, such security flaws need to be fixed immediately. Forescout has reached out to major vendors to fix the vulnerabilities but first, such flawed devices have to be identified and that's a major hassle. As many IoT devices don't have a software bill of materials (SBOMs), it is hard to find out if any software in the device is vulnerable.
"Because of the absence of a software bill of materials, it is often very hard to determine whether a vulnerable software is in a device. Conversely, when vulnerabilities get discovered, it is very time-consuming to contact all potentially affected vendors," Andrei Costin, co-founder and CEO of Binare, which specializes in securing IoT devices before deployment, told Bank Info Security.
That's the reason, Forescout has started working with ICS-CERT, Federal Office for Information Security of Germany (BSI), CERT Coordination Center, the JPCERT Coordination Center beside the U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA). The firm has also reached out to the open-source managers to issue the fixes.









