Security vulnerabilities exist on all devices that can be connected to the internet. Some mitigate the risks by patching any security holes that exist while others are not very quick. That eventually leads to hackers compromising the system. Similarly, smart televisions too can be hacked and at the moment TCL smart TVs running the Android TV operating system seem to be vulnerable with backdoors, affecting millions of users.
Two cybersecurity researchers dug deep into the world of smart TVs to study the cybersecurity infrastructure and were stunned by TCL's lackluster security flaws. Sick Codes, a white-hat hacker and John Jackson, an application security engineer at Shutterstock, a photo-licensing company found that TCL smart TVs' entire file system could be accessed over Wi-Fi through undocumented TCP/IP port. Besides that, the files could also be overwritten without any authentication (no username and password needed).
"I can wholeheartedly say that there were multiple moments that I, and another security researcher that I met along the way, couldn't believe what was happening. On multiple occasions I found myself feeling as though, you couldn't even make this up," Sick Codes wrote in a blog post.
Major Security Flaws
The main security hole in TCL smart TVs running Android OS is that the entire file system is on an unsecured HTTP connection, meaning it could be accessed by anyone on the internet — even from a phone. That way, you could get access to a TCL smart TV's file system remotely without even being on the same Wi-Fi or local network. Tom's Guide was provided a URL, allowing them to access the entire file system of a TCL smart TV in Zambia — all of that over the internet using an Android phone's Chrome browser.
Sick Codes and Jackson reported two vulnerabilities — CVE-2020-27403 and CVE-2020-28055 — to the U.S. Computer Emergency Response Team (US-CERT). By exploiting the two vulnerabilities, a hacker could upload a malicious APK or gain access to the TV and can "perform fake system upgrades by writing to the /data/vendor/upgrage folder." Apart from that, the hacker can also download most system files that could comprise sensitive information such as credit card number, name, billing address, email address and phone number.
A Chinese Backdoor?
The fact that TCL is a Chinese TV manufacturer, raises a few questions if the company deliberately left the backdoors. The two researchers found Terminal Manager Remote, an app on the TCL TV that had configuration files with server listings. It could handle screenshots of TVs, files and logs. One of the servers also included TCL firmware updates and it needed no authorization to access.
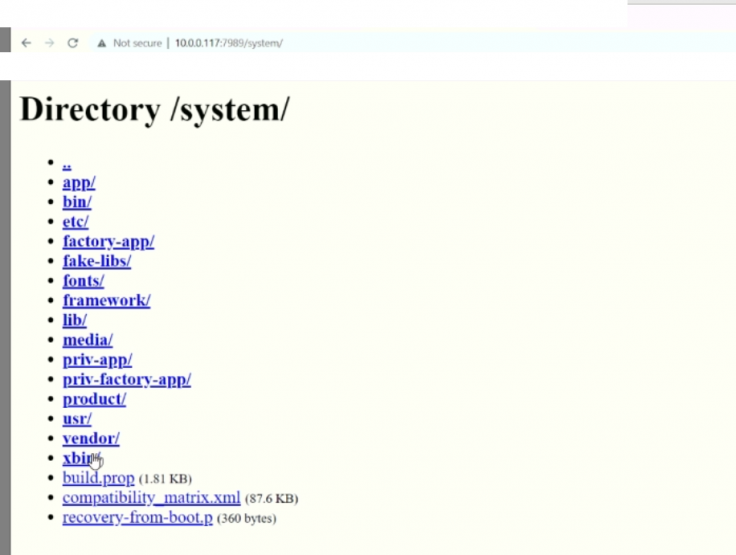
The server list was divided into four regions — mainland China; Asia-Pacific region; Middle East, Africa and Europe; North and Latin America. However, it was not clear if the servers were configured to send or receive files. "It is a Chinese backdoor," Sick Codes said.
Silent Patch Released
The two researchers contacted TCL on October 16 but didn't get a response until October 29. In an email addressed to them, Eric Liang of TCL said that the company had released a patch after receiving the report from them. "Here is how is it going on now: A new version to fix this vulnerability is going to release to SQA on Oct. 29 (UTC+8). We will arrange the upgrade plan after the regression test passes," the email said.
However, the quick fix could not impress the two researchers as there was no further communication and the patch was released without notifying anyone. The update didn't change the firmware version either.
"They updated the (TCL Android) TV I was testing without any Android update notification or warning. This was a totally silent patch — they basically logged in to my TV and closed the port," Sick Codes told the Security Ledger, adding that it was proof that TCL had remote access to the TV sets.
"This is a full-on back door. If they want to, they could switch the TV on or off, turn the camera and mic on or off. They have full access," he added.









