Microsoft's Windows is the most popular and widely used operating system in the world. But it is also the most vulnerable among the lot. Despite recent improvements, Windows still has vulnerabilities that have often been exploited by hackers. The recent one has been exposed by Google's bug-hunting team named Project Zero.
Google's security experts have found a zero-day vulnerability in Windows Kernel Cryptography Driver (cng.sys) that is actively being targeted by hackers. Tracked as CVE-2020-17087, the vulnerability is present in Windows 7 and Windows 10 since the 1903 update that was released in October 2019.
Actively Used by Hackers
After discovering the bug, Google's team gave Microsoft a week to fix the vulnerability. However, Microsoft didn't respond in time, leading Google to disclose the problem. As per Google's cybersecurity researchers Mateusz Jurczyk and Sergei Glazunov, hackers can exploit the vulnerability to escalate the user's access privilege in Windows, allowing the attacker to take over the system.

"The bug resides in the cng!CfgAdtpFormatPropertyBlock function and is caused by a 16-bit integer truncation issue. It was tested on an up-to-date build of Windows 10 1903 (64-bit), but the vulnerability is believed to be present since at least Windows 7. A crash is easiest to reproduce with Special Pools enabled for cng.sys, but even in the default configuration the corruption of 64kB of kernel data will almost surely crash the system shortly after running the exploit," they clarified.
Google's team said that bug helped hackers escape Chrome's sandbox, a restricted testing environment. By combining the two bugs, hackers could escape the mode and install malware on the system. Google fixed the sandbox in Chrome browser bug last week.
Hackers' Target Unknown
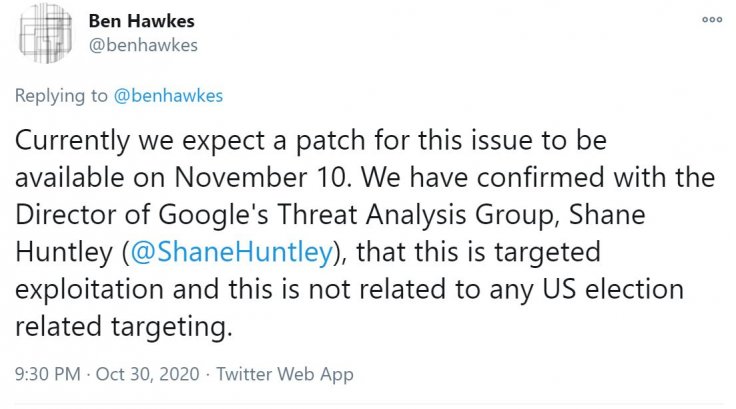
While Google said that the hackers were actively exploiting the bug, it wasn't sure what their target was. However, they added that the target was not associated with the U.S. Presidential Election. The team expects a fix from Microsoft by November 10. Microsoft in a response to TechCrunch said that the attacks were "very limited and targeted in nature" and the company didn't see any "evidence to indicate widespread usage."
This is the latest security flaw in Windows 10 this year. In January, the U.S. National Security Agency (NSA) found a zero-day vulnerability in Windows 10's cryptographic API. While there was no evidence that it was exploited, in June and September, two more bugs were discovered that were being actively exploited.
Another bug was discovered in September that allowed one-click access to servers. Called Zerologon vulnerability, hackers were exploiting the bug to take over servers. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) warned about the issue which was discovered by researcher Tom Tervoort at Secura. For both vulnerabilities, Windows released patches quickly.









