A group of Chinese hackers, known as APT 41, has been allegedly targeting online gaming companies, technology firms and think tanks in the U.S. The Department of Justice (DoJ) alleged that seven members of the group had launched cyberattacks on over 100 companies and government agencies for ransom.
Seven members of the group included five Chinese nationals and two Malaysian businessmen, who were charged on Wednesday (September 16, 2020) for the cyberattacks that also included spying on Hong Kong protestors.
The DoJ charged two of the alleged Chinese hackers — Zhang Haoran and Tan Dailin — in August 2019 while three others — Jiang Lizhi, Qian Chuan, and Fu Qiang -- were indicted last month. All five Chinese nationals are fugitives while the Malaysian authorities arrested the unnamed businessmen, who were executives of SEA Gamer Mall, last month.

Is APT41 State-Sponsored?
All five members of APT41 are either current or former employees of Chengdu 404 Network Technology which specializes in cyber security. The company provides 'white hat' services to companies to detect vulnerabilities in the network.
One of the hackers, Jiang Lizhi, has allegedly boasted about his links to Chinese Ministry of State Security as per the DoJ. Known as "Blackfox", he had also worked for a hacking group that served the Chinese government agencies. Chengdu 404 has also listed a government tech security agency and Chinese universities as its partners. Another hacker, Tan Dailin, was also associated with antivirus company Anvisoft with a dubious origin.
As per the court documents, APT41 is also known as "Barium," "Winnti," "Wicked Panda," and "Wicked Spider." They mainly targeted video game companies outside their clientele. While the group seems to attack companies for financial benefits, FireEye, a cyber security company, said that APT41 also targeted firms in various industries including telecom, media and healthcare.

Although, the DoJ did not provide a strong link between the group and the Chinese government, it said the Chinese Communist Party (CCP) had turned a blind eye to such hackers.
"The Department of Justice has used every tool available to disrupt the illegal computer intrusions and cyberattacks by these Chinese citizens," Deputy Attorney General Jeffrey Rosen said. "Regrettably, the Chinese communist party has chosen a different path of making China safe for cybercriminals so long as they attack computers outside China and steal intellectual property helpful to China."
Past Activities
In recent times, APT41 has mainly exploited the known vulnerabilities including the Citrix's CVE-2019-19781, known security flaws in Cisco, D-Link routers, Pulse VPN products and Zoho ManageEngine Desktop Central. Citrix ADC's vulnerability was recently exploited by unknown hackers in a German hospital for a ransomware attack that led to the death of a patient.
Once they had access to a system, APT41 would deploy malware and encrypt the network demanding a ransom. The hackers also stole source codes, code signing certificates and customer data that they could resell.
APT41 has also been seen deploying cryptojacking tools to mine cryptocurrencies in compromised systems. However, their main focus remained on video game companies. They have often targeted such firms in order to steal digital game currencies and items. The Malaysian businessmen were probably linked with APT41 for the latter.
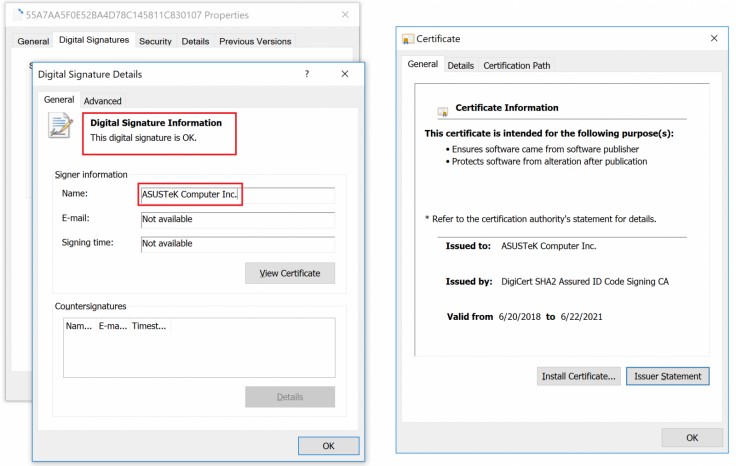
The group was also named the preparator in the cyberattack at Taiwan based company Asus. The hackers created a backdoor and digitally signed the Asus Live Update Tool using the company's own certificates to push the update in thousands of computers, affecting millions of users. Kaspersky first noticed the backdoor. It enabled them to access those compromised systems later.









